By Bader Youssef & Bassem Youssef
About a week ago, I stopped by my local bank’s ATM machine. As I lined up behind a couple of other customers, I felt an air of tension and unease. The woman at the ATM machine was glancing cautiously at people behind her through the mirrors placed on the machine. Although I understood her caution, I wondered if she knew that a more threatening thief might not be directly behind her. Rather, the thief could be sitting comfortably at home reading the sensitive data off of her ATM card through a magnetic strip skimmer while obtaining her PIN number with a tiny, thermal camera placed on the ATM machine.
According to the U.S. Secret Service, thefts from ATM skimmers now total more than $1 billion per year. This statistic does not take into account the possible, large number of unreported incidents, that could raise this number to the multiples of billions.
Just last June, in Putnam County, Florida, an organized criminal group was able to compromise 291 credit cards from ATMs before being apprehended by authorities.
ATMs are arguably much more valuable than gas station pumps due to the volume of FIAT that they deal each day. Using the NEM Catapult blockchain and Internet of Things (IoT) context awareness, we can protect ATMs from the inside out by giving each ATM a way of sensing for unwanted external components and reporting unauthorized access or modification.
How does ATM skimming & shimming work?
ATM skimming works much in the same way that gas station pumps are skimmed — through internal, or external devices that are able to read either the magnetic strip or card chip. From there, the skimmer sends the data over SMS or Bluetooth to the criminal’s own laptop or phone.
Often times, criminals will place external covers, keypads, and card readers over legitimate ones on the ATM. Usually, these are very hard to spot because they are an exact copy of the ATM’s parts.


These covers contain simple electronics, mainly a magnetic strip reader, to intercept the card going into the machine. To steal the PIN number, criminals will also place a low-power thermal camera over the keypad to see which numbers have been pressed. Once they have this stolen information, the criminal can now easily create cloned cards to spend online or in stores.
However, while the well-known skimmer is a popular choice for crooks, another device has been making its way into ATMs: Shimmers. Shimmers operate on the same principle of a skimmer, but is instead a much lower profile device that can fit in the credit card reader itself. As one can imagine, it becomes very hard to detect compared to an external component. Shimmers also can read the supposedly secure chip-based cards, making them all the more threatening.

Detecting Fake & Fraudulent ATM Parts With IoT Context Awareness
Using the security and transparency of blockchain, and the automation and unbiased reporting from Internet of Things, we can construct a solution that combats skimmers, shimmers, and everything in between!
Firstly, let’s take care of the physical aspect of the problem: the placement of skimmers and shimmers on and in the ATMs. Applying our proprietary “IoT Skin” on the ATM, we can cover all areas of interest, including the inside of the cabinet. The IoT Skin applies concepts of context awareness to monitor its environment and take note of and act on outside variables. \ Context awareness is the ability for a system, the IoT Skin in this case, to detect and react to its surrounding environment. A monitoring device inside of the ATM watches the IoT Skin for changes in outside conditions, such as pressure, light, and the distance of objects around the ATM.

If the IoT Skin detects any objects being placed over certain areas, such as near the card reader or keypad, for an extended amount of time, the ATM’s owner is notified to examine the ATM for skimmers. To combat shimmers, part of the Skin is placed on the inside of the card reader itself.
The IoT Skin would have measures in place to tell the context of the situation happening on the outside or inside of the ATM. For example, if someone were to lean on the machine for thirty seconds to a minute, the Skin wouldn’t be triggered. However, if a presence is detected for more than five minutes, then the IoT Skin knows that fraudulent activity may be taking place. Even if the presence is no more than a piece of gum stuck on the outside of the machine, it will prompt the ATM staff to examine the ATM and ensure nothing illicit has been placed.
In other words, the IoT Skin is able to be aware of the context of the situation, differentiate between different types of activity, and act accordingly to alert the correct parties in the case of suspected fraud.
This same monitoring device also utilizes a smart lock and magnetic reed sensor to further protect the inside of the ATM. These security measures secure and watch for any time an ATM is opened by a legitimate (or illegitimate!) company, and they ensure that the interaction is authentic and valid.
Now, where is all this information going? How is everything being validated and authenticated? The answer: The Catapult blockchain!
Using Catapult’s built-in features, we can have the IoT monitoring device directly log all important external and internal interactions on the blockchain’s secure, distributed ledger, as well as facilitate access to the inside of the ATM.
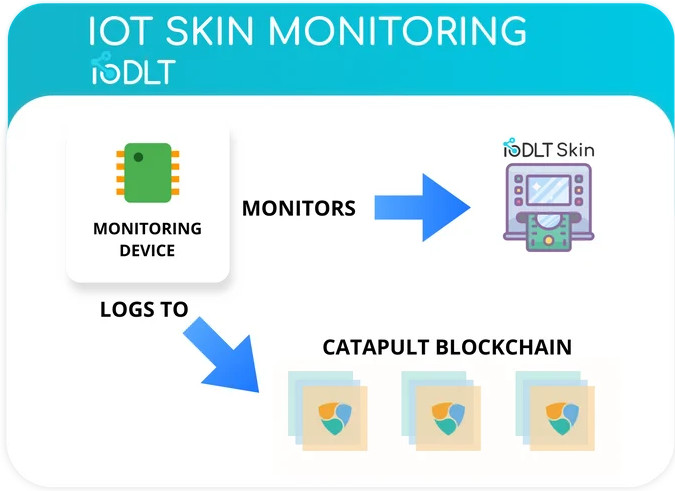
The IoT monitoring device that monitors the IoT Skin logs all interactions to the blockchain, keeping an immutable and certifiable record of any suspicious activities, or if nothing happened that day, that the ATM is considered safe and is labeled on the blockchain as such. To help consumers easily discern the safety of an ATM, a scannable NFC or QR tag would be placed to allow for the consumer to view the ATM’s history on Catapult. This transparency would inspire confidence and trust for ATM customers. They would know the exact provenance of the ATM that they are using, and that it is immutable-ly recorded and verifiable on the blockchain’s distributed ledger.
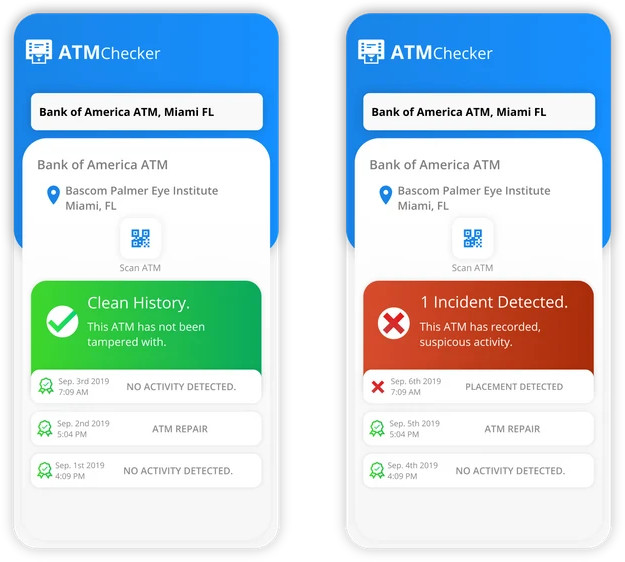
ATM Access Control – Facilitated by Catapult
Now that nothing can be placed externally, what’s to stop someone from opening the ATM and placing a skimmer from the inside, should they gain access? Access control for ATMs are crucial. Whether it is to simply refill the machine with cash, or even to modify a part of the ATM, only qualified individuals should be allowed to perform these actions.
To solve this problem, ATM operators must own an on-chain, non-transferable certificate, called a “Mosaic” on Catapult.
This certificate is issued by a company who has a unique domain on Catapult, called a namespace. Once a namespace is created, its name can’t be used by another person on the blockchain. On-chain Mosaic Restrictions are also used for access control to only allow qualified individuals to own and use this certificate. They act as network-wide rules and standards that apply to each operator and define which machines they are allowed to service. These restrictions can also allow for specific cases where the operator may not utilize the certificate, such as at specified locations or timeframes. Therefore, companies can issue non-transferable, programmable certificates under their namespace to the correct people to prove they are legitimate!
Upon each interaction between the operator and ATM, a one-time smart contract, called an Aggregate Bonded transaction, will also be issued between the ATM operator and the ATM owner before the ATM is to be serviced. In this on-chain contract, they will agree on a timeframe and location for the specific ATM. This contract also contains a secret, encrypted code that the IoT device will ask for as part of authentication. Given that this contract can also execute multiple types of transactions all at once, the contract will assign the operator’s Account Metadata (another feature on Catapult!) the timeframe and location of the ATM that they are supposed to service.
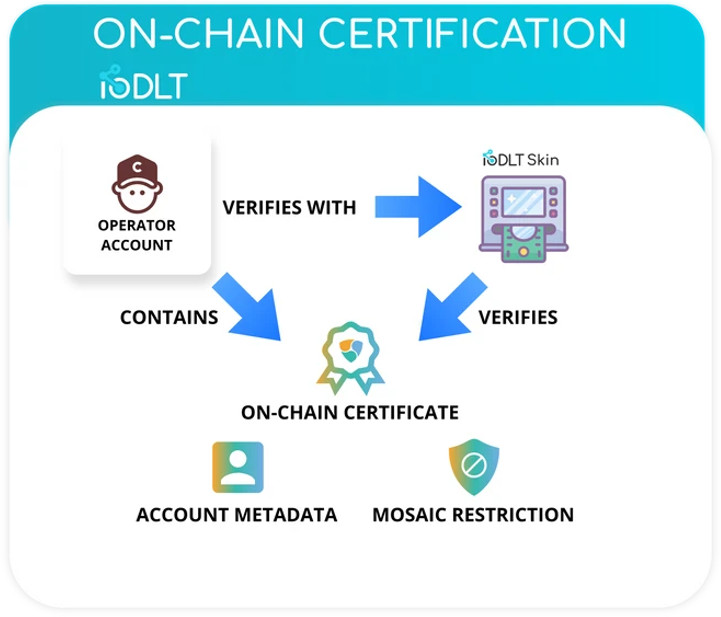
After checking the certificate of the operator and the secret code, the IoT device checks the account’s metadata for the correct data to ensure that they are at the correct location, and within the time frame agreed upon the smart contract. Once this is confirmed, the aforementioned smart lock is unlocked. The magnetic reed sensor also confirms that the door was opened for a reasonable amount of time, further validating the interaction.
If everything checks out, the IoT device logs the interaction as valid on-chain. If it wasn’t valid, that would also be logged, and would alert the ATM owner or other involved parties. The Catapult blockchain now keeps an immutable record of this interaction on-chain, and is able to be referenced and accessed anytime in the future if needed.
Keep in mind that even if a criminal element working for the operator decides to place a skimmer, our IoT Skin will be watching on the inside, ensuring nothing out of the ordinary has been placed.
Any time an operator needs to refill cash, perform maintenance, or modify the ATM, the access control mechanism will control every aspect of the ATM, from the inside-out.
Combined with the IoT Skin, this multi-layer solution creates a tightly-controlled and monitored environment that will deter any criminal as soon as they catch sight of our trackable, IoDLT QR code ID tag. Win-win!
Conclusion
The combination of the Catapult blockchain and IoT is a powerful one — it allows us to connect the real-world with the digital one, providing a new perspective into many different industries. Protecting ATMs from an ever growing threat is just one application — there are many more that can come out of applying this same concept of direct IoT-to-blockchain communication to different problems.
This technology enables the verification of unbiased technology to properly record data onto a secure, immutable, and fault tolerant ledger, which in turn inspires consumer confidence and business savings.
Bader and Bassem are the founders of IoDLT, a blockchain-powered IoT solution. For more information or business contact, please email [email protected]
About IoDLT
Founded in 2018, IoDLT (Internet of Distributed Ledger Technology) utilizes two disruptive technologies – Internet of Things and blockchain – to provide seamless, secure, and scalable B2B solutions. IoDLT brings security to small and large businesses alike, without compromising user data privacy and user-to-business interactions. Their technology’s application spans a wide range of industries, namely healthcare, agriculture, supply chain, and energy metering.
Alongside providing business solutions, IoDLT envisions a future run by embedded devices. Securing those devices will become imperative to the operations of any business. IoDLT deploys proprietary and affordable IoT to blockchain protocols to secure the devices of the world